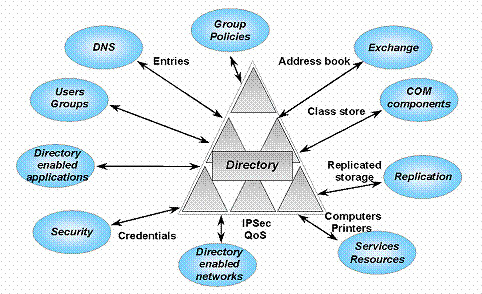
Active Directory Conditional Access is a powerful security feature designed to protect valuable data in an organization. It provides a means to safeguard access to assets, such as cloud applications, networks, and on-premises systems, while reducing the risk of data breaches from cyber-attacks. With the proper implementation of Active Directory Conditional Access, organizations can ensure their data is only accessed by users with pre-defined permissions. This helps to dramatically reduce the risks associated with unauthorized access, such as data breaches, ransomware, and other cyber threats. By combining user authentication and conditional access policies using Active Directory, organizations can rest assured that their data is safe and secure at all times.
1. Boost Your Security with Active Directory Conditional Access
Having proper access control measures in place is essential for both IT security and employee productivity. Active Directory Conditional Access is an effective way to ensure both. With Conditional Access, security measures are enforced before granting access to corporate applications.
By using Conditional Access, you can boost your security by protecting against malicious users and unauthorized access while still allowing legitimate users access to the applications they need. Here are a few of the beneficial security features:
- Multi-factor authentication: adding an extra layer of authentication, increasing security
- Geo-location based access: setting restrictions on the areas from which users can access corporate applications
- Dynamic authorization: granting access based on user identity, device and application status
In addition to increased security, Conditional Access also helps reduce the amount of time spent managing access scenarios. This leads to fewer manual procedures which in turn gives your IT security team more time to concentrate on other security pinch points.
2. Protect Your Network with Easy-to-Use Access Control
Take Action
To ensure maximum protection of your network, you must use access control. This type of security controls how data is accessed in an organization. It restricts user access to data and network resources, depending on user privileges. Here are some easy-to-use access control providers that will guarantee the security of your data:
- SSH Security & Access Control - SSH, short for Secure Shell, is one of the most effective ways to secure your network. It offers advanced user authentication and access control to monitor and restrict network activity.
- Passwordless Logins – With passwordless logins, an individual can sign up or log in with biometric authentication. It eliminates the need to remember complicated passwords and makes it much easier to manage user access.
- Network Security & Access Control Protocols – Protocols such as RADIUS and TACACS+ allow a network administrator to define and enforce access control policies. These protocols also enable secure communication between the client and the server.
Implement Your Security Measures
Once you decide which access control provider to use, it’s time to implement it. Start by putting in place a system to monitor user access and restrict certain privileges. You should also configure your network elements to ensure that users are not gaining unauthorized access to sensitive data. Finally, make sure to periodically update and review your access control policies to ensure that they are still effective.
3. Enjoy Flexible Access and Enhanced Security with Conditional Access
Protection of Your Data and Control of Access
Conditional access has revolutionized the way businesses and their employees can access data. Easy and secure authentication and authorization processes ensure that only the people and applications with the appropriate clearance can see confidential information. This gives the flexibility to access data whenever and wherever needed while protecting data from unauthorized access.
Added on to the convenience and security is the control conditional access provides. Organizations can set timelines, dynamic profiles, and thresholds when granting or denying access to data. As layers of permission and authorization can be built in, businesses are able to tightly restrict what users can actually access and use.
Features of Conditional Access
• Multi-factor authentication: Add an extra layer of authentication to limit access to only the rightful user.
• Granular access control: Decide which app and services people can access and which fields on specific records they can see.
• Access settings: Specify the time range and location from which a user is able to access data.
• Denial of access: Users can be completely blocked from accessing a particular app or record.
• Device control: Restrict access to data based on device type or platform.
• IP address blocking: Deny access to particular IP addresses, while allowing access from approved locations.
4. Keep Your Data Safe – With Conditional Access!
Not All Access Is Equal
It is essential to ensure that only authorized personnel have access to sensitive data and systems. Conditional access is a tool that can be used by IT departments to make sure that users can only access resources when certain criteria are met. This might be from a certain location or on a certain device. With conditional access, IT teams can ensure that only those with the right credentials can gain access to the data they need and nothing else.
Security at Scale
Conditional access offers better security and reliability at scale. IT departments can have access to an analytics dashboard that provides insights into how the security systems are performing in real-time, allowing them to make adjustments on the fly. This helps to ensure that no unwanted access or data loss occurs. Additionally, conditional access can also be used in combination with multi-factor authentication for added security. With the right tools, organizations can keep their data safe and secure.
Q&A
Q: What is Active Directory Conditional Access?
A: Active Directory Conditional Access is a technology used to ensure that only approved people can access a computer network or system. It ensures that only users with the right credentials are given access to the network and that they follow certain security protocols.
Conclusion
Protecting corporate data with Active Directory conditional access is crucial in today’s business environment. With LogMeOnce, you can create a secure environment that leverages Active Directory conditional access for data protection, allowing you to increase your business’s security. Signing up for a FREE LogMeOnce account enables you to easily proactive segregation of duties, comprehensive access control, improved compliance and better secure corporate data from unauthorized access in an Active Directory conditional access environment. Don’t wait, sign up for a FREE LogMeOnce today and secure your corporate data with the ultimate security of Active Directory conditional access.